Infrastructure Support for Public Cloud Service
by Manfred Chan
What are public, private and hybrid clouds?
Public clouds are services based on the standard cloud computing technology to provide flexible and on-demand computing and network resources to the general public over the internet.
A public cloud deployment model is different from a private network. Public clouds, such as Microsoft Azure and Amazon Web Services share a computing infrastructure among different users, business units, etc. However, such environment may not be suitable for all businesses, especially those having mission-critical workloads, security concerns, uptime requirements or management demands. Instead, enterprises integrate the public cloud environment with their private clouds at their existing data centers to form hybrid clouds; and provision computing and network resources on their hybrid clouds from their on-premises networks.
Why use a public cloud service?
The main benefits of using a public cloud service are:
- Allow easy, fast and inexpensive setup for new applications
- Flexible in scaling up and down the resources to meet the demands
- Reduces the wasting of the computing capacity
To design the infrastructure to support the public cloud integration, we need to know to what extent the cloud service is needed to communicate with the on-premises network. In fact, the data traffic pattern of the cloud service is the major concern in this respect.
There are three major network traffic types to take care of when building services with public clouds, first is the data traffic that are generated by clients, applications and/or services, second is the traffic communicating between the public cloud and the on-premises services, and last is the management traffic which are used for server management, configuration and monitoring, etc.
If the services are designed solely to be accessed from off-premises anywhere in the world and all the IT services are served from the public cloud, there is no need to set up a network connection between the on-premises and the public cloud. Users can access the services/applications directly from the public cloud service. The administrators can also manage the service through the cloud interface.
However, for most enterprises having a hybrid cloud setup, there are many server management services, authentication service like active directory or LDAP, remote desktop service, SIEM, server/application monitoring service, configuration management service and security management services needed to communicate with the on-premises servers. In this regard, a reliable and secured network tunnel has to be established to fulfil these needs.
Almost all public cloud services have VPN support for the aforementioned scenarios. Some cloud services even support dedicated lease lines to facilitate high bandwidth requirements. There are two configuration types of the VPN tunnel, namely, Point-to-Site (P2S) and Site-to-Site (S2S). The P2S configuration can create a secure connection from an individual client computer to a virtual network and is mainly used when the connection is from a remote location such as home or branch office that needs to be connected. P2S connections do not require a VPN device or a public-facing IP address in order to work. The VPN connection is established by starting the connection on-demand from the client. But it is seldom used in the enterprise environment.
The second connection type is S2S connections. It can be used for cross-premises and hybrid cloud environments. S2S VPN is more common for enterprises because a permanent secure tunnel is always required for day-to-day operations.
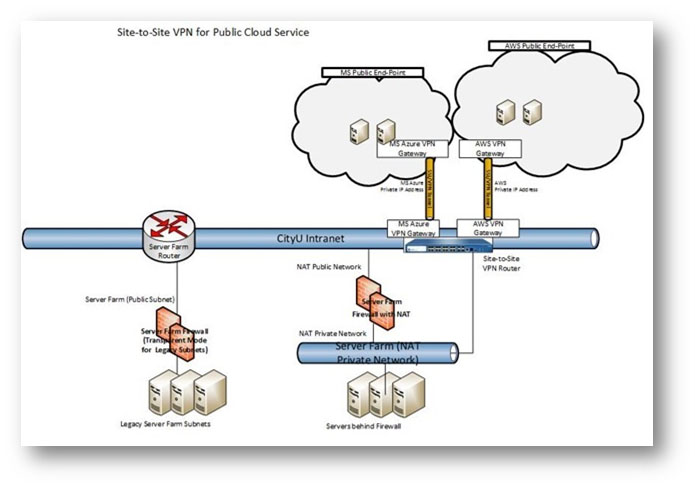
In the above diagram, a dedicated S2S VPN router is engaged to set up a secure VPN tunnel for one or more public cloud services. To avoid single point of failure, a pair of VPN routers, which are configured in Active-Standby mode, will be used. In all cases, the management traffic will be redirected to this VPN tunnel to access the on-premises server farm network from the public cloud. In this architecture, network traffic must be routed via the on-premises firewall so that all traffic can be controlled, protected and monitored accordingly.
Focusing on server management, some considerations are outlined here to determine whether management servers should reside in the public cloud or the on-premises.
- If the management servers only support the public cloud, they should be located in the public cloud. It does not make sense to place them in the on-premises.
- If the management servers support both the public and private clouds, in most cases, those major server components should be located in the on-premises and the gateway servers reside in the public cloud.
- If the management servers only support the private cloud, no network traffic should be allowed from the on-premises to the public cloud.
In short, integrating the public cloud into the on-premises network allows fast deployment with flexible demand in network and computing resources. It can cope with the future trend in extending the on-premises data center to a hybrid cloud environment.