Advanced Persistent Threat (APT)

characteristics. These days, APT is often used to describe advanced or complex intrusive cyber attacks against specific
targeted organizations over a long period of time.1
mass volume of sensitive information such as source coding, trade secret and personal
information which usually help the attacker gain a definitely advantage, identify of a
weakness or to certain extend gain an upper handover victim of the attack:
2. UniversitiesUniversities
3. Financial institutions
4. Government entities.


|
With these characteristics, APT attacks are different from conventional hacking. In conventional hacking, the attackers can be individuals who are picking targets randomly and are using popular hacking tools or readily available scripts. Their motives are either for fun (defacing web sites) or monetary gain (stealing credit card information). They will move on to try another target if they fail to break in after spending certain effort. For APT, the modulus operandi of is quite different from conventional hacking. First of all, the profile of the attackers can be state or country affiliated organized syndicates. Bejtlich elaborated that the objectives of their attacks can be political (maintaining stability), economic (stealing intellectual property), technical (gaining access to source code for further exploit development) or military (identifying weaknesses for military advantages). |
After identifying a target organization, the attackers will engage in reconnaissance to study the infrastructure of the target, the employee profiles and even the business partners of the target trying to identify some potential attack points. Attackers will then try different means to penetrate into the target. A typical method is to craft a spear phishing email containing malicious payload which can bypass anti-malware detection. To increase the chances of the target clicking the malicious link or opening the attachment, attackers spend a lot of time researching the phishing target and the target system. Information is mined from a variety of sources including corporate blogs, Google searches, social media sites, etc. 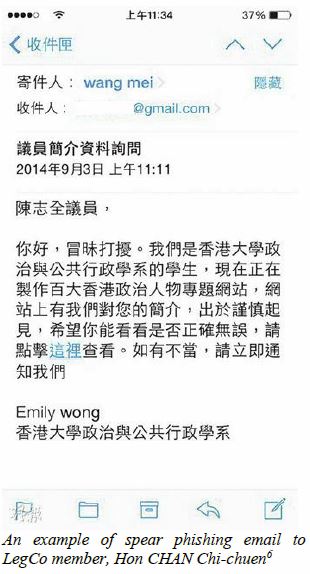
|

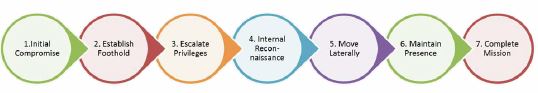
Initial Compromise - Represents the methods that attackers use to penetrate a target organization’s network using methods such as exploiting vulnerable Internet-facing web servers or spear phishing (An electronic message sent to a targeted victim with personalized message content which contains a malicious attachment, a link to a malicious file, or a link to a malicious website).
Establish Foothold – Attackers will access and control one or more computers within the victim environment. Backdoors will be installed which are used to establish an outbound connection from the victim’s network to a computer controlled by the attackers.
Escalate Privileges – Involves acquiring credential items that will allow attackers to access more resources within the victim environment. Techniques such as password harvesting and cracking methods will be used. Attackers will try to gain access to privileged and administrator accounts.
Internal Reconnaissance – This is the stage when attacks will collect information about the compromised computers in order to obtain information about the internal network, users, groups, trust relationships, files and documents. Attackers may perform directory or network share listings, or search for data by file extension, key word, or last modified date. File servers, email servers, and domain controllers are customary targets of internal reconnaissance.
Move Laterally – Attackers will move laterally within a network to compromise more computers in order to search for data that they want.
Maintain Presence – Attackers will install backdoors to continue control over the computers remotely from outside network. These backdoors could be different from the ones during Establish Foothold stage in order to make them difficult to identify and remove all of their access points. Attackers are also skillful enough to cover their traces of compromise by deleting activity logs and encrypting communication traffic.
Complete Mission – Once the attackers are successful in finding files of interest on compromised computers, they often pack them into archive files and transfer out using FTP, custom file transfer tools or backdoors.

There are massive amount of computer systems in Universities, and Universities are operating IT environments quite openly. Unlike corporate enterprises, not all systems are centrally protected based on a consistent set of tightened security policies. Different faculties and departments may house their own systems and may even ignore implementing proper security protections.
Attackers sometimes find University computer systems easer to penetrate than corporate enterprises. They will use these compromised computer systems as intermediate stepping stone to attack the real targeted organizations in order to create difficulty in tracing attack source of origin.
Some attackers may have interest in research data and hence target to compromise certain computer systems in the Universities in order to gain access to those data. There are also times when attackers will launch attack against Universities to steal personal information which can facilitate them to create more sophisticated phishing email targeting the real victims of corporate enterprises.
Since APT attacks are becoming more common, Universities should be more aware of such threat in order to better defend against APT attacks.

In addition, staff and student should change their password credentials often regardless of whether Universities are enforcing a periodic password change policy. Staff and student should also set different password credential across all University systems, external web applications and social media sites. This will reduce the impact if one of these systems is compromised leaking out credential. If feasible, two-factor authentication should be enabled (e.g. remembering the sign-on device, using token, etc.) to increase the difficulty of compromising a computer.
Universities can also consider deploying web application firewall or even APT protection / detection systems. Rule set tuning will be required to configure these systems to work properly in order to reduce false alarms. The security architecture should be designed in such a way that firewalls, IPS / IDS, web application firewall or APT protection/detection systems work in layered defense mode.
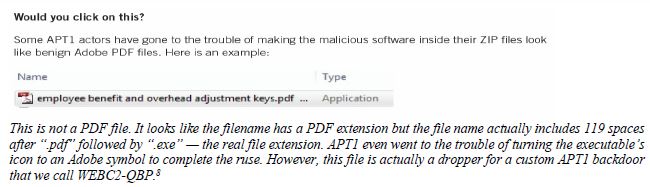

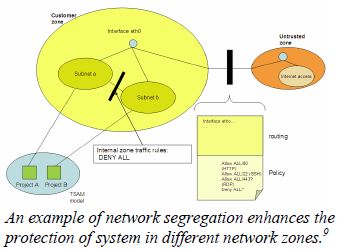
4. Monitor Suspicious Traffic
APT attacks involve call back traffic. Also, attackers will remotely control the compromised computers by connecting to the installed backdoors. If such network traffic can be monitored and identified, the indicator point of compromise (IOC) can be quickly reviewed. Having said that, it may not be easy to differentiate the call back and remote control traffic because attackers can encrypt the traffic and use the well-known ports for communications.
APT protection / detection systems are specialized in detecting and even blocking such kind of traffic. Some IPS / IDS are also capable of detecting unusual traffic patterns. Universities can consider implementing these solutions at appropriate network access points.
5. Improve Incident Response Capability
No organizations are immune to cyber attacks. In fact, corporate enterprises are beginning to shift to a new mindset that they need to prepare for the worse that they can become a victim target. It is imperative for Universities to define an incident response process. Because the attack can compromise systems, networks and applications, the process should be backed by a taskforce consisting of representatives from IT teams. The team should be trained to respond to suspected and confirmed attacks, contain the compromised environment, collect logs and evidence, and perform forensics investigation.

-
"Understanding the advanced persistent threat” Jul. 2010. Web. 08 Sept. 2014
-
"South Korea Probe Says North Behind Cyber Attack: Report" AFP. 09 Apr. 2013. Web. 04 Sept. 2014.
-
"The Real Story of Stuxnet" David Kushner. 26 Feb. 2013. Web. 04 Sept. 2014.
-
"Verizon 2013 Data Breach Investigations Report, 20% of external data breaches tie to state affiliated groups. " 2013. Web. 04 Sept. 2014.
-
"US-China cyber espionage comes under increased scrutiny" Ivan Fursov, RT. 07 Nov. 2013. Web. 04 Sept. 2014.
-
"Ming Pao News, phishing email to LegCo Hon CHAN Chi-chuen" 04 Sept. 2014. Web. 04 Sept. 2014.
-
"Top 7 Phishing Scams of 2013” 26 Dec. 2013. Web. 04 Sept. 2014.
-
"Mandiant Releases Report Exposing One of China’s Cyber Espionage Groups" 19 Feb. 2013. Web. 04 Sept. 2014.
-
"IBM Tivoli Service Automation Manager – Extension for Juniper SRX Firewall, Background to the Firewall Extension" Web. 05 Sept. 2014.
-
"Problem Profile Bulletin: Malware Threats" June. 2014. PDF. 05 Sept. 2014.
-
"Spear Phishing the News Cycle: APT Actors Leverage Interest in the Disappearance of Malaysian Flight MH 370" 24 Mar. 2014. Web. 08 Sept. 2014