Main navigation
News
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Cloud computing is a computing style in which scalable and flexible IT functionalities are delivered as a service to external customers using Internet technologies. Cloud ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ The following security recommendations or guidelines help secure your server: 1. Rename the Administrator Account - Renaming the Administrator Account will help to prevent a brute ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ 1. Consider Using a Firewall For the network hosting the Terminal Server, it is best practice to use a firewall capable of stateful packet inspection. A firewall capable of ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Vulnerabilities in Remote Desktop Connection Vulnerabilities have been discovered in the Microsoft Remote Desktop Connection which could allow an attacker to take complete control ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Continuous advancements have been made to improve Remote Desktop security; however, universities still remain as a major target for exploiting Remote Desktop vulnerabilities: 1 ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that enables users to interface with another computer through a graphical interface. RDP is based on ...
by Joe Lee
Introduction The Committee on Information Services and Technology approved the Electronic University Data Regulations 1 on 19 August 2010. Faculties and staff are obliged to protect “all data collected, maintained and used in the University's information systems.” In addition to observing related ...
by Kevin Chan
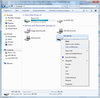
With the mobile workforce growing continuously, it is a major concern for IT decision makers to protect sensitive data on mobile computers. Starting from Windows Vista, BitLocker Drive Encryption helps protect sensitive data from being accessed by unauthorized users. BitLocker To Go extends such ...
by Clevin Wong
In recent years, due to the proliferation of low cost mobile devices like notebook/netbook computers and Wi-Fi phones, more and more people use these devices for communication and Internet access via the wireless networks. However, wireless networks are insecure by nature. In wireless networks, data ...
by Wilson Wong
Introduction World Wide Web is growing extremely fast in the past few years. Counting only the number of new websites responding to an online web server survey has already recorded an increase of 2,137,329 in June 2009 (a jump from 235,890,526 to 238,027,855). The actual number of websites in the ...