Main navigation
News
December 2018
by P Y Fung (FMO), Joseph Ng (ESU)

As part of an initiative to build a smart campus, the Carpark Management System at the Bank of China (Hong Kong) Complex (BOC), Yeung Kin Man Academic Building (YEUNG) and Lau Ming Wai Academic Building (LAU) have been upgraded with the video analytics technology. The new Carpark Management System ...
by Andes Cheung
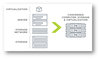
Introduction CityU currently maintains its own datacenters to provide an IT infrastructure supporting diverse services for teaching, research, administrative, and management use. Dated back a few decades ago, we have adopted a three-tier architecture consisting of compute, storage and networking ...
by Vicker Leung (OCIO)

In our previous issue ( Ref: Network Computing Issue 97 – October 2018 ), we introduced the newly designed CityU Mobile v2, covering the enhanced UI design, the technologies used in the core, as well as new capabilities like checking room availability, retrieving library loan records, etc. These new ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Authentication is the process of identifying the authenticity of a user. It can be accomplished by means of a combination of login ID (identification) and password (authentication ...
October 2018
by Alex Lam

It is very common nowadays for students and staff to access research data, journals and courses online offered by other education institutions or companies over the Internet. The access usually requires users to sign up and create different user accounts. This article will detail how the Computing ...
by Cyril Ha
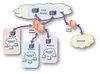
Background? Information System Security has been a key concern over the past many years as more and more business processes rely on Information Technology to operate. Alike many other organizations, the usual first line of defense would be Internet protection with security devices such as a ...
September 2018
by Vicker Leung (OCIO)

It has been more than a decade since Apple launched the first iPhone. Since then, the growth of the mobile landscape has never ceased. In 2018, there are 3.5 billion active smartphones worldwide, and it is estimated to reach 5 billion by 2023, which is equivalent to 65% of the global population [1] ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ More and more transactions are performed online. Thus, a secured connection has to be ensured between the server and the client. However, connection mainly requires just a server ...
June 2018
by S K Tsui

What is IoT? The Internet of Things (IoT) refers to billions of network devices, sensors and actuators around the world capable of gathering data (e.g. temperature, location, etc.) from the environment and sharing the data across the Internet. The data collected will then be analyzed, processed and ...
by Yuki Tam (OCIO)

Over the past few decades, systems and their data were protected by usernames (IDs) and passwords. However, this is not considered as safe anymore. An attacker can impersonate a user easily when a password or the password database is stolen. Even if the passwords are safely kept, an attacker can ...