Internet Security Protection at CityU
Since many easy-to-use and powerful Internet applications are now readily available, more and more people in CityU are making use of the Internet for their daily studies, researches and electronic communication of all forms. In addition, with an increasing number of students living in hostels, the network communication between CityU and the Internet had risen significantly.
With the high volume of Internet traffic and network connections, plus the increasing number of virus/worm, hacking and attacking activities throughout the Internet, the security protection at our Internet gateway has become an important and serious concern to the Computer Services Centre (CSC).
Protection at CityU's Internet Gateway - Intrusion Protection System (IPS)
In order to protect CityU from Internet attacks, the CSC has deployed a number of measures to enhance the speed, stability and redundancy of the Internet connection. However, this article will only focus on a newly deployed system - the Intrusion Protection System (IPS).
The following simplified diagram briefly depicts various network devices currently implemented between the CityU gateway and the Internet.
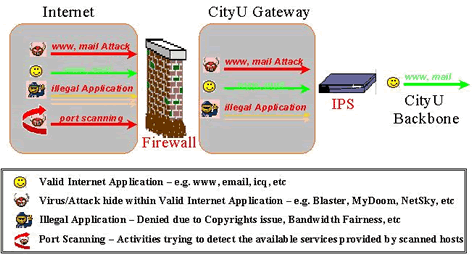
Why do we need IPS?
As can be seen in the diagram above, CityU has already implemented a firewall to protect itself from Internet attacks. So why do we still need to deploy the IPS?
Firewall is like a network traffic filter or a policy enforcer to either permit or block some predefined Internet applications or protocols. Firewall does not examine in depth the contents of network packets that are being configured to pass through.
This means a firewall cannot prevent attacks hidden within the network traffic that are allowed to pass through it. For example, it is very common to configure a firewall to allow email traffic to come through, but if the attack is hidden within an email, it will be able to pass through the firewall. This explains why so many Internet attacks were spread via email, even with the deployment of firewall.
Principles of an IPS
The IPS was designed to overcome the limitations of the firewall. IPS works by examining in detail the contents of every network packet. With different detection mechanisms and correlation between potential attack packets, the IPS can detect intrusion which are otherwise very difficult to be discovered by the firewall alone. Some of the attack detection mechanisms are listed below:
-
Signature based detection
-
Check each network packet against known attack signatures
-
-
Network Protocol Anomaly
-
Detect any deviation from the protocol standard
-
-
Denial of Services (DoS) Detection
-
Compare abnormal high traffic against prolonged traffic statistics
-
-
Spooling Attacks
-
Detect any abused use of IP addresses
-
-
Honey Pot
-
Devices installed purposely to trap, detect and study the network attacks
-
By adopting the above advanced detection mechanisms, any attack passing through the firewall can then be caught by the IPS. Depending on the actions reacted against the detected intrusion, an IPS can be configured as follows:
-
Intrusion Detection Mode (Intrusion Detection System)
-
Report and Log the attacks
-
Can be in
-
Sniffing Mode (IPS listens to tapped or mirrored traffic only)
-
In-Line Mode (Traffic passing through the IPS directly)
-
-
The packet can still pass through the network as normal, even if intrusions are being detected
-
-
Intrusion Protection Mode
-
Report and Log the attacks
-
Must be in In-Line Mode
-
Drop the attacking packets at once
-
Roles of Firewall and IPS
Although the IPS can detect a large number of Internet attacks, it cannot replace the firewall. IPS and firewall should work together to provide maximum protection to the network. In fact, they play different roles in safeguarding the network where one complements the other:
-
Firewall is based on the network policy to filter out all disallowed network traffic from entering the protected network.
-
IPS examines the remaining traffic based on a number of detection mechanisms to filter out Internet attacks
Features of IPS in CityU
In the following section, we shall introduce the features of the IPS deployed in CityU. With the help of real examples, it shows how the IPS can protect the CityU from daily Internet attacks.
1. Detect and Report Intrusion in Real Time
The mission of the IPS is to detect intrusion once it is detected. As it needs only a few packets to compromise a system, the IPS must block the attack in real time. On the other hand, not all detected intrusions are critical, some of them are informational and there is no need to block the traffic. As a result, we need an interface to define the policy of the IPS. Based on the severity of the attacks, we can report, log or drop the intrusion based on our pre-defined IPS policy.
As shown in Figure 1-1, a network administrator can define the blocking policy for each intrusion. Different policies can be applied for both inbound and outbound attacks.
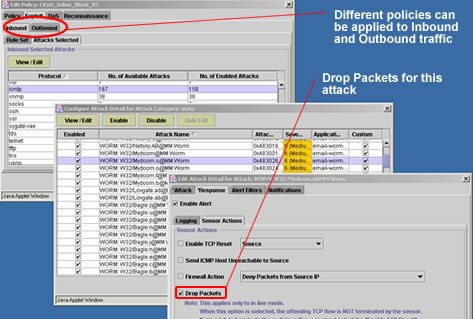
Figure 1-1 Policy Editor to define IPS policy (The above policy will drop Incoming MyDoom.S Worm)
Based on the defined policy, the IPS will detect and block the intrusions accordingly. A real-time console will display the detected attacks as shown in Figure 1-2 below.
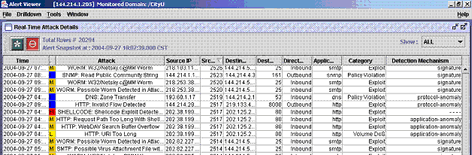
Figure 1-2 Real Time detection of Intrusion
2. Provide a flexible and configurable real time console for attack Query and Correlation
Since there are so many intrusions detected everyday, we need a flexible and configurable interface for the display, query and backtrack of the attack database. An example of the real-time console has already been shown in Figure 1-2.
In addition, intrusions can be identified according to protocols, OS, severity, direction, source IP address, destination IP address; the real-time console should be able to manipulate the attack database based on these properties. This feature is shown in Figure 2-1 below.
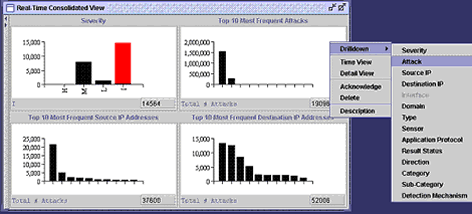
Figure 2-1 Attacks in Real-Time Console can be manipulated according to different fields
Furthermore, the attacks may have worked in sequence in order to compromise a system. We may want to group or drill down some of the inter-related packets in order to study the attacking mechanism. Figure 2-2 shows how the real-time console of the IPS can provide this function.
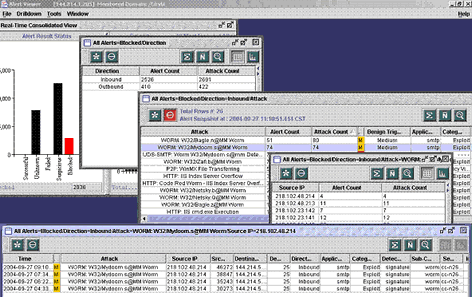
Figure 2-2 DrillDown View of an attack (Blocked->Inbound->MyDoom.S Worm->Source IP)
3. Protect against DDoS attack
Distributed Denial of Service (DDoS) is an attack that makes use of a large number of hosts to generate many simple but fast network packets to a few hosts. This results in a large volume of network traffic or connections reaching the destination host(s) which render the target machine(s) run out of its capacity to handle its normal services - a denial of services.
As mentioned before, every single attack in a DDoS is very simple and would not be normally classified as an attack. In order to detect such an attack, IPS will need to baseline normal traffic volume and report a DDoS attack once the traffic deviate greatly from the normal traffic. Figure 3 illustrates how the IPS detects a DDoS attack.
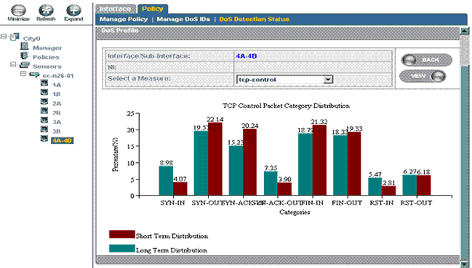
Figure 3 DDoS detection mechanism - referring to baseline traffic statistics
4. Automatic update of attack Signatures
Like anti-virus software which requires the latest virus signatures to protect against new viruses, IPS also needs to update the attack signatures from time to time. This should be done automatically and transparently to the network administrator. The scheduled updates of signatures are shown in Figure 4 below.
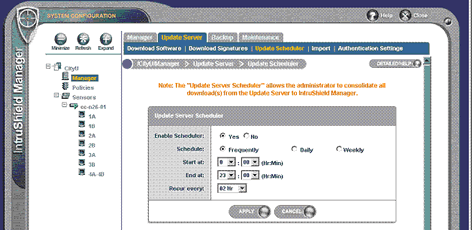
Figure 4 Scheduled Tasks to update attack signature automatically
5. Capture attack packets
In order to study the details of intrusion and provide evidence for the attacks, it is very important to capture the attack packets for further reference. Figure 5 shows just how it can be achieved in the IPS.
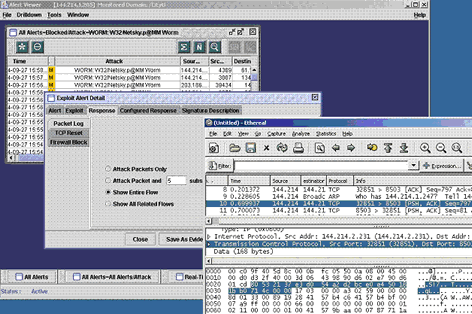
Figure 5 Intrusion detected can be captured and displayed using Sniffer Format
6. Generate Management and Summary reports
All network management system must provide both summary and detailed reports to record jobs done. The IPS provides both real-time and scheduled reports to network administrators based on the attacks stored in the attack database. The generated reports can be displayed as HTML documents or saved as PDF files.
Conclusion
With the wide spreading of viruses, worms over the Internet, the security protection at the CityU Internet gateway was indeed a very serious concern. In view of this, the CSC had deployed a number of measures and the latest technologies to handle the Internet security issue.
The use of both firewall and the newly deployed IPS has shown that many Internet attacks have been successfully blocked. This results in a more reliable and secure Internet environment for all users of CityU.
However, everyone in CityU should also take the responsibility to protect his/her own computers by applying the latest patches, updating the latest antivirus software, etc. This simple but important measure is always the key to enhance the total secure level of the CityU network and thus improves the productivity of all members of the CityU.