DDoS Protection of JUCC
by Wilson Wong, S K Tsui, Alex Lam
A Distributed Denial-of-Service (DDoS) attack is a cyber-attack, which an attacker tries to overload the targeted server/system with a huge volume of traffic from multiple, distributed sources (usually zombie computers), making the server/system unavailable to its intended users. As the attacks come from a large number of PCs in different areas, it is impossible to stop these attacks simply by blocking accesses from an area. To mitigate the damage from a DDoS attack, a pool of devices that scrutinises inbound traffic before it hits the targeted system is required.
According to the
published by Deloitte, the number of DDoS attacks in 2017 will become large in scale, harder to mitigate, and more frequent. They expect that there will be over 10 million DDoS attacks in total globally. In view of the increase in the number of DDoS attacks against Hong Kong's local universities, the Joint Universities Computer Centre (JUCC) has decided to employ the DDoS protection services from Nexusguard with an aim to ensure uninterrupted services in the local institutions of higher education.
Starting from the second half of 2016, the Computing Services Centre (CSC, CityU) has been working with Nexusguard to implement the DDoS protection for the university’s IT services. Technically, there are several types of DDoS attacks, such as SYN, TCP, HTTP floods and Domain Name System (DNS) attacks, which attack different parts/layers of the IT infrastructure. The protection platform of Nexusguard is thus comprised of three pillars, namely Application Protection, DNS Protection and Origin Protection, to block attacks on different components of the IT infrastructure. We shall briefly discuss them in turn below.
Application Protection
Application Protection provides DDoS protection for web servers by scrutinising traffic in the Nexusguard’s Scrubbing Centres.
Application Protection provides DDoS protection for web servers by scrutinising traffic in the Nexusguard’s Scrubbing Centres.
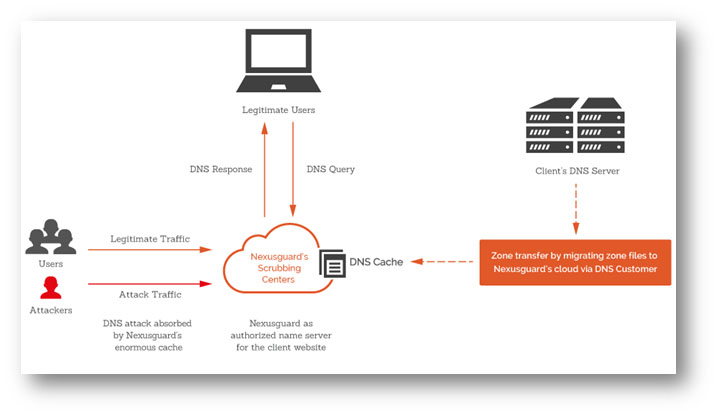
By changing the DNS record, all traffic to the web servers will be redirected to the scrubbing centre first. If in case there is a DDoS attack against the protected web servers, the scrubbing centre, which is equipped to handle huge volume of traffic, will filter all the attacks and pass only the legitimate traffic to the protected web servers by means of reverse proxy. Thus, the protected web servers can continue to provide services to users without any interruption.
Currently, the CityU Announcement Portal (CAP) is protected via the Application protection service. We will put other central web servers under the same DDoS protection in the near future.
DNS Protection
The DNS is a hierarchical decentralized naming system to translate a host name into IP address(es) connected to the Internet.
The DNS is a hierarchical decentralized naming system to translate a host name into IP address(es) connected to the Internet.
We utilise Nexusguard’s DNS protection service to protect CityU from DNS attacks by transferring the zone file of the “cityu.edu.hk” domain to the Nexusguard’s DNS cluster and including Nexusguard’s DNS cluster in the authoritative name server list of the “cityu.edu.hk” domain.
By leveraging anycast technology and redundant caching, Nexusguard’s solution performs load balancing across their high-performance, global DDoS Mitigation Network to filter out and absorb all DNS attacks and malicious traffic, including:
- DNS Amplification
- NXDomain
- Phantom Domain
- Random Sub-domain
- Look-up Domain
Origin Protection
In addition to launching web application and DNS attacks, attackers may perform a volumetric attack that aims to consume all the available Internet bandwidth and resources of the University. The latter is a typical example of a volumetric DoS or DDoS attack that will effectively block the network connectivity between the Internet and all campus users.
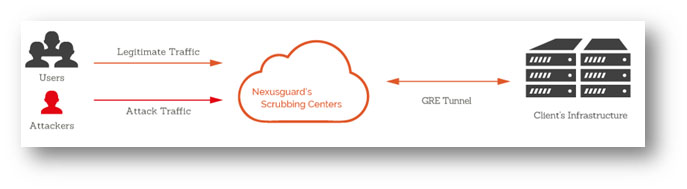
“Origin Protection” is a solution that aims to protect against volumetric DoS or DDoS attacks by making use of the BGP routing protocol to redirect all CityU’s Incoming Internet network, including both legitimate traffic and attack traffic, to the Nexusguard’s worldwide scrubbing centres.
These worldwide scrubbing centres, which collectively equipped with over 1.44Tbps of mitigation capacity, have significant capability and intelligence to “clean out” the attack traffic. The resulting legitimate traffic will then be routed back to CityU via the dedicated GRE tunnels. Thus, the University will be protected from DoS and DDoS attacks that are becoming more common in the Internet environment.
Conclusion
The implementation of the above three pillars of protection is still in the process of fine tuning. It is expected to be completed in the third quarter of 2017. If staff or students experience any issues, especially when using the CityU Announcement Portal (CAP), please contact the CSC by sending an email to csc@cityu.edu.hk.