Main navigation
News
- Academic Regulations and Records Office
- Computing Services Centre
- Department of Computer Science
- Department of Electrical Engineering
- Department of Information Systems
- Department of Marketing
- Enterprise Solutions Office
- Facilities Management Office
- Finance Office
- Human Resources Office
- Internal Audit Office
- Office of the President
- Office of the Vice-President (Administration)
- Research Grants and Contracts Office
- Run Run Shaw Library
- School of Law
- Shenzhen Research Institute
- Student Development Services
- Talent and Education Development Office
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ IaaS includes the entire computing infrastructure resources stack from the facilities to the hardware platforms that reside in them. It provides limited application-like features ...
by Samuel Wong

Every day, a large amount of sensitive information and data are being transferred through emails or movable devices. S ecurity threats increase as emails are uncontrollable after leaving the senders while movable devices can be lost or stolen easily. Hence, i t is important to secure sensitive ...
by Tony Chan
Microsoft launched its latest web browser Internet Explorer 9 (IE9) in mid-March 2011. In comparison with IE8 and IE7, IE9 is clearly faster, cleaner and safer than its predecessors. In addition, Microsoft has derived a table to show that IE9 outperforms some rival browsers in terms of performance ...
by Joe Lee
The Computing Services Centre (CSC) announced on 25 May 2011 that the university will cease the support of Windows Vista (Win Vista, SP1 and SP2) upon the termination of support for Vista SP1 by Microsoft starting August 2011 (a ctually, Microsoft officially terminated the support of Win Vista SP1 ...
by Wilson Wong
It is always recommended that a strong password should be used to resist guessing and brute-force attacks and lower the risk of security breach. An account with a weak password, such as a word in dictionary, can easily be broken by a hacker. He/She may then read, modify or delete all your files and ...
by Mei-ling Lee, Edward Chan
Today, we are living in a mobile world and our students are using their mobile devices to communicate electronically whenever and wherever they desire. To make use of the latest mobile technologies for their university learning and to take advantage of the high performance and reliable full campus ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Cloud computing is a computing style in which scalable and flexible IT functionalities are delivered as a service to external customers using Internet technologies. Cloud ...
by Dick Wong
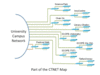
Due to a shortage of space, the university is exploring various ways to accommodate new staff and academic programmes. One way of tackling this problem is to adopt a “core-satellite” approach. The “core” represents premises in the Kowloon Tong main campus while “satellite” refers to remote offices ...
by Alex Lam
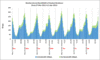
Overview Since the setup of student residence in year 2000, the number of users has grown from 800 to about 2800 this year. Furthermore, with the completion of phase 4 early next year, the number of residents will be further increased to around 3500. With the increase in the population and ...
by Ellen Chan

Administrators of three local tertiary educational institutions shared their technical experience at a forum to discuss crucial technology enhancements to support the new 4-year curriculum.