Main navigation
News
December 2016
by Joe Chow
? The Policy Concept Windows policy, better known as Group Policy, is a feature of all Microsoft Windows operating systems (…Windows 7, Windows 8.1, Windows 10…) that controls the working environment and behaviour of a system. For example, a policy setting that allows or disallows remote access to ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ ? According to a study conducted by IBM in 2012, it costs an organization US$80 per defect if vulnerabilities are identified early during the development stage, but the cost ...
September 2016
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ ? “Successful businesses understand the value of timely, accurate information, good communications and secrecy. Information security is as much about exploiting the opportunities ...
June 2016
by by Henry Wong

With all staff mailboxes migrated to Office 365 (O365), the migration of on-premises email supporting tools is underway. One significant upgrade is the migration of on-premises email anti-spam tool to the O365 Exchange Online Protection (EOP) cloud-hosted email filtering service. The migration has ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ ? Relationship with ISMS Information Security Management System (ISMS) is defined in the ISO/IEC 27000 set of standards. The ISO/IEC 27001 standard sets out a certifiable and ...
by JUCC ISTF
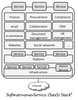
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ ? The NIST Definition of Cloud Computing 1 The cloud model is composed of 5 essential characteristics (Ondemand self-services; Broad network access; Resource pooling; Rapid ...
March 2016
by ML Lee
In today’s office environment, we often share information like reports, presentations and minutes among colleagues. We have been taught how to connect to the departmental share drive through a network drive letter to store and access files in a traditional file folder structure. This works quite ...
by JUCC ISTF
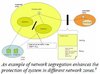
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ The term APT was first used by U.S. Air Force back in 2006 to facilitate discussion about a set intrusion activities with specific characteristics. These days, APT is often used ...